When experts claim the sky is falling, we point out that you're just looking at the ground.
Tuesday, June 26, 2012
ACM MedCOMM from Start to Finnish
Tule mukaan Helsingissä!
Join us at the ACM Workshop on Medical Communication Systems!
We don't just love repeating letters mid-word—we are practicing our Finnish for the first ACM SIGCOMM Workshop on Medical Communication Systems (ACM MedCOMM) to be held in Helsinki, Finland on August 13.
MedCOMM brings together scientists, engineers, standards-committee members, patient advocates, security researchers, pickled herring, students, and medical experts to evaluate the state of the art in communications for medical applications. We'll talk about how to build systems with better security, spectrum utilization, interference properties, power consumption, and patient-friendliness than what exists today. We'll draw people and insights from the SIGCOMM community, where last year's "best paper" concerned medical-device security and involved software radio, jamming, and some fundamental full-duplex radio action.
Check out the lineup of invited talks and papers and join us for this full-day event in Helsinki on August 13! The draft PDF program complete with visuals provides further details on speaker bios, implants, etc.
You can register by July 9 to save €40 off the registration fee—and you'll also get a week's free passage on public transportation in Helsinki.
Täytyy harjoitella enemmän suomenkieltä!
Tuesday, June 19, 2012
Baxa's Non-Approved Software Policy: That's Your Problem
FDA regulations require manufacturers to “Validate all changes, updates, and patches, including operating systems, before installing them to ensure the safety and effectiveness of the medical devices.”1 Baxa ExactaMix Compounders have been verified and validated only with the software that was installed by Baxa. Thus, any changes to the original, validated image, including installation of antivirus software, nullifies the validated state, may create an unsafe operating condition, and would constitute off‐label use.
As an FDA‐regulated manufacturer, Baxa Corporation will not/cannot support nor endorse off‐label use of its compounder. Only validated systems are approved by Baxa as being safe and effective for use. Any unauthorized programs installed on a Baxa product will void the manufacturer’s warranty. ExactaMix Compounders have been validated only with the operating system and patches installed by Baxa. Installing any software not provided by Baxa, including OS updates, firewall software and anti‐virus products, on Baxa automated compounding devices may change the operating parameters and adversely affect the operation of the device, rendering it unsafe to use.
The footnote above points to an FDA document titled Reminder from FDA: Cybersecurity for Networked Medical Devices is a Shared Responsibility, of which Baxa has adopted a very narrow interpretation that maximally reduces their responsibility for software security. How convenient.
While the quote that Baxa pulled from the document is really there, it does not tell the whole story. Rather than taking the draconian stance on the issue of software configuration that Baxa suggests, the document also explicitly states that, "Medical device manufacturers and user facilities should work together to ensure that cybersecurity threats are addressed in a timely manner." and furthermore that:
The need to be alert and responsive to cybersecurity issues is part of the device manufacturer’s obligation...Software patches and updates are essential to the continued safe and effective performance of medical devices. Typically, FDA approval is not required before install changes, updates, or patches that address cybersecurity issues (see question #10 of the guidance).
Other highlights from the FDA document include these two bullet points that appear to directly contradict Baxa's stance on software updates:
- Make sure that you have adequate anti-virus software and firewalls installed, properly set up and current.
- Update your operating system and medical device software. Software updates offer the latest protection against harmful activities.
In fairness to Baxa, the FDA guidance does not make it entirely clear what the company's responsibilities are in terms of validation for software updates and antivirus software, but a blanket mandate that customers must not take vital steps to protect their devices or patients seems like an irresponsible choice by a manufacturer that could put patients at risk. Rather than sharing responsibility as FDA recommends, Baxa is completely abdicating responsibility for security and forcing customers to do the same by forbidding them to install software updates.
Monday, June 18, 2012
A Fluke of Security Issues from Updating Software on Windows-Based X-Ray Testers
Imagine you'd like to test X-ray machines in a hospital, dental office, etc. for safety and calibration. X-ray testers come into play. So how does one maintain the software used with X-ray testers? How do you know that you've downloaded the legitimate software?
The TNT 12000 X-Ray Test Device from Fluke Biomedical distributes its software updates online. Worried about the security of your hospital network while downloading software? Concerned that installing software might violate your hospital's corporate security policies and get you in hot water with your CIO or CISO if you accidentally download malware? No problem. Trust the Internet. Just download the .EXE file or the ZIP file using any shared Internet connection from an HTTP site. No need for connection-oriented SSL security or pesky end-to-end digital signatures of integrity-protected content. Another time saver for increased productivity.
The TNT 12000 X-Ray Test Device from Fluke Biomedical distributes its software updates online. Worried about the security of your hospital network while downloading software? Concerned that installing software might violate your hospital's corporate security policies and get you in hot water with your CIO or CISO if you accidentally download malware? No problem. Trust the Internet. Just download the .EXE file or the ZIP file using any shared Internet connection from an HTTP site. No need for connection-oriented SSL security or pesky end-to-end digital signatures of integrity-protected content. Another time saver for increased productivity.
Saturday, June 16, 2012
Philips Medical Patient Monitors and Downloading Medical Device Software
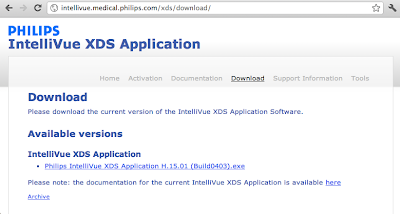
Earlier this year after speaking about medical device security at a Semiconductor Research Corporation event, I got the gift of food poisoning that landed me in an ER. I enjoyed a warm IV and a Philips Medical Intellivue patient monitor. As I writhed in pain, I wondered how the hospital updated the medical device software.
Here's how. Download an unsigned .EXE file from Philips Medical.
What could go wrong? Don't worry because a 2009 FDA MAUDE adverse event report on a different product explains that "Philips Medical Systems is not responsible for ... the integrity of the ... system infected with a computer virus." The MAUDE report seems to conflict with the spirit of Philips Medical's own product security policy. Philips Medical deserves kudos for writing a security policy document; not too many medical manufacturers can claim to have a policy on software security. However, Philips Medical may wish to hold off on claims of having "security designed in" if the same document later says:
Here's how. Download an unsigned .EXE file from Philips Medical.
What could go wrong? Don't worry because a 2009 FDA MAUDE adverse event report on a different product explains that "Philips Medical Systems is not responsible for ... the integrity of the ... system infected with a computer virus." The MAUDE report seems to conflict with the spirit of Philips Medical's own product security policy. Philips Medical deserves kudos for writing a security policy document; not too many medical manufacturers can claim to have a policy on software security. However, Philips Medical may wish to hold off on claims of having "security designed in" if the same document later says:
In many of our products, we provide you with a controlled update repository to reduce the risk of equipment outage due to unauthorized or faulty anti-virus signature updates.Many? Many is a euphemism for we're sorry that we cannot quantify our cybersecurity preparedness. There is a diffusion of responsibility between hospitals and manufacturers that leads to certifiable finger pointing over security of medical devices. It has already been almost a decade since Philips discussed the problem of medical device security. Let's hope that achieving reasonable medical device security doesn't take as long as it took physicians to accept the advice of Semmelweis et al. on the importance of hand washing. That was 1847. And hand washing is still a problem.
Friday, June 15, 2012
FDA Recalls Attributed to Software Failures
Today FDA released its FY2011 OSEL Annual Report. Of relevance to medical device software, Figure 5 on page 22 charts the impact of software on medical device recalls. The figure indicates that last year, about 24% of FDA recalls of medical devices were attributable to software failures. The report also proposes an analogue to "flight data recording" to get better introspection into adverse events on medical devices (page 39).
Thursday, June 14, 2012
Secure Software Updates for Medical Devices?
[In April 2010, I wrote the following incomplete draft post about software updates for medical devices after the automatic anti-virus snafu in hospitals. More than two years later, I figure it's time to release this paragraph warts and all.]
Software updates are hard to write well. One example is the McAfee update that reportedly caused thousands of computers to get stuck repeatedly rebooting. I am often asked why it's hard to automatically securely update software on a medical device. I think the example from McAfee is illustrative: what does a person do when a software update goes awry? For a desktop computer, one can call tech support and grab a cup of coffee until the computer is repaired. With a medical device, there is much less room for error and the consequences of downtime (or erroneous operation) potentially higher. Software updates are hard to get right for personal computing, and software updates for medical devices have less wiggle room for error.
Software updates are hard to write well. One example is the McAfee update that reportedly caused thousands of computers to get stuck repeatedly rebooting. I am often asked why it's hard to automatically securely update software on a medical device. I think the example from McAfee is illustrative: what does a person do when a software update goes awry? For a desktop computer, one can call tech support and grab a cup of coffee until the computer is repaired. With a medical device, there is much less room for error and the consequences of downtime (or erroneous operation) potentially higher. Software updates are hard to get right for personal computing, and software updates for medical devices have less wiggle room for error.
Friday, June 8, 2012
Click Here to Download Your AVEA Ventilator Software Update. Trust Me.
[Updates contributed from readers appear at the bottom of this blog post.]
Hospital IT staff: How much do you trust the Internet for updating medical device software? A number of researchers in software upgrades bemoan the general state of the art for secure software updates. Worse, the cryptographic technology at the core of commercial software update mechanisms is broken and being actively exploited by the Flame virus.
Well, if you work for a hospital, the Flame virus is probably the least of your worries. You just want to keep your HIT systems and software-controlled medical devices working. Vendors routinely install software updates for medical devices from the Internet or USB keys. I've seen medical sales engineers download pacemaker-related software from the Internet.
Today I tried to download a software update for CareFusion AVEA Ventilators. What I found may disturb hospital IT staff. Here's a screenshot. When I clicked on the highlighted link for "AVEA Ventilator software update," a second dialog box popped up, "Warning: Visiting this site may harm your computer."
What's this second dialog box? It's a feature in the web browser that uses the Google Safe Browsing service. For this particular web server that provides the software update for a ventilator, Google had the following data for www.viasyshealthcare.com:
I find it difficult to establish trust in the safety of software affilatied with reports of "malicious software being downloaded and installed without user consent."
What's the way forward? That's a longer discussion. Let me update you over drinks. For starters, go read the Google papers on web malware [Trends in Circumventing Web-Malware Detection and All Your iFRAMEs Point to Us]. Here's to a better and more secure software update infrastructure. Cheers.
Summary: The web server distributing the software updates for a ventilator (a medical device) itself needs some help with software updates. According to Google, the web server was infected with 48 viruses and 2 scripting exploits. 20 pages resulted in malicious software being downloaded and installed without user consent.
The risks should be obvious. This is an update for a medical device, and yet one must download it in a manner as if software sepsis is no big deal. Health care professionals might as well stop their washing hands while they're at it.
Hospital IT staff: How much do you trust the Internet for updating medical device software? A number of researchers in software upgrades bemoan the general state of the art for secure software updates. Worse, the cryptographic technology at the core of commercial software update mechanisms is broken and being actively exploited by the Flame virus.
Well, if you work for a hospital, the Flame virus is probably the least of your worries. You just want to keep your HIT systems and software-controlled medical devices working. Vendors routinely install software updates for medical devices from the Internet or USB keys. I've seen medical sales engineers download pacemaker-related software from the Internet.
Today I tried to download a software update for CareFusion AVEA Ventilators. What I found may disturb hospital IT staff. Here's a screenshot. When I clicked on the highlighted link for "AVEA Ventilator software update," a second dialog box popped up, "Warning: Visiting this site may harm your computer."
What's this second dialog box? It's a feature in the web browser that uses the Google Safe Browsing service. For this particular web server that provides the software update for a ventilator, Google had the following data for www.viasyshealthcare.com:
What happened when Google visited this site?Of the 347 pages we tested on the site over the past 90 days, 20 page(s) resulted in malicious software being downloaded and installed without user consent. The last time Google visited this site was on 2012-06-08, and the last time suspicious content was found on this site was on 2012-06-03.
Malicious software includes 48 trojan(s), 2 scripting exploit(s).
Malicious software is hosted on 3 domain(s), including nikjju.com/, lilupophilupop.com/, koklik.com/.
This site was hosted on 1 network(s) including AS26651 (CAREFUSION).
Wonderful. I am downloading ventilator software from a web server known to have 48 trojans and 2 scripting exploits. Hurray for science and technology. Clicking on the CAREFUSION link provides further assuring data:
What happened when Google visited sites hosted on this network?On the same site, I found another product that discusses its software update mechanism for Cortical Stimulator Control Units. The company advises its customers to "Click Run" when the "File Download Security Warning" dialog box appears. The instructions appear to refer to a CD rather than an Internet download, but I wonder how many technicians take a short cut by downloading an update via the Internet. That Internet is so darn convenient.
Of the 3 site(s) we tested on this network over the past 90 days, 2 site(s), including, for example, viasyshealthcare.com/, sensormedics.com/, served content that resulted in malicious software being downloaded and installed without user consent.
The last time Google tested a site on this network was on 2012-06-08, and the last time suspicious content was found was on 2012-06-06.
I find it difficult to establish trust in the safety of software affilatied with reports of "malicious software being downloaded and installed without user consent."
What's the way forward? That's a longer discussion. Let me update you over drinks. For starters, go read the Google papers on web malware [Trends in Circumventing Web-Malware Detection and All Your iFRAMEs Point to Us]. Here's to a better and more secure software update infrastructure. Cheers.
Subscribe to:
Posts (Atom)